
Why Use Secured Network Services?
Contact a full-service IT security company for secured network services. It will assign a dedicated team to your project. You

Contact a full-service IT security company for secured network services. It will assign a dedicated team to your project. You
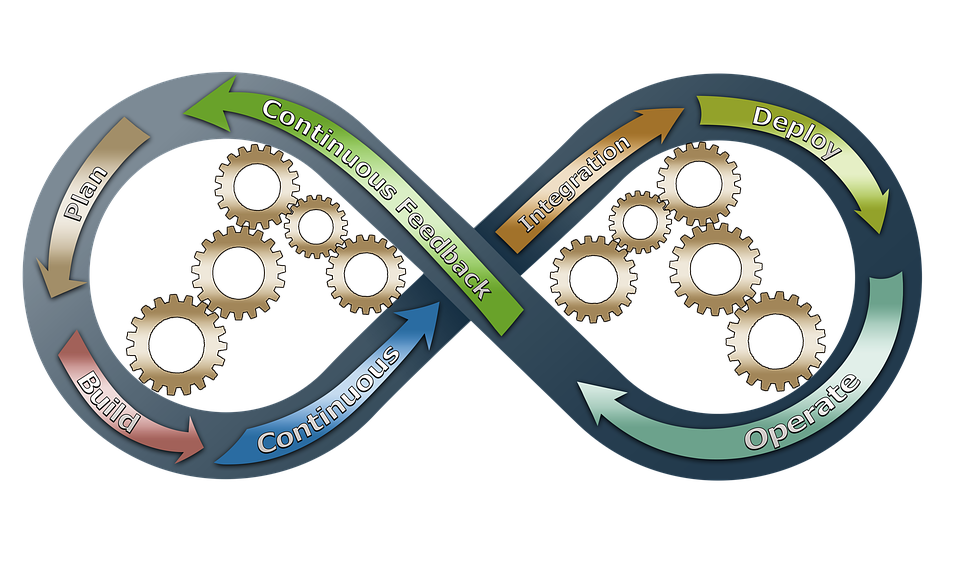
To prevent the unauthorized use, alteration or falsification of protected content, a variety of cryptographic techniques can be used. Cryptographic
The network for GSM is called PLMN (Public Land Mobile Network). It is connected to the Public Switched Telephone Network
If you own a business or are a network administrator, finding the best network management system for the specific system
Copyright © 2025 | Powered by Atsco